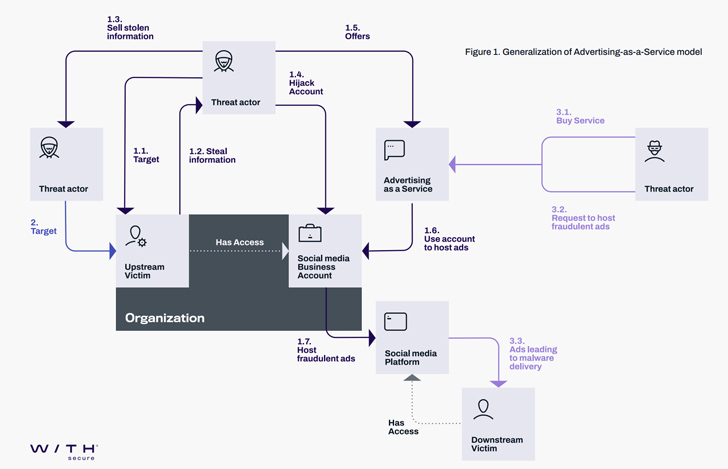
Malicious actors related to the Vietnamese cybercrime ecosystem are leveraging advertising-as-a-vector on social media platforms corresponding to Meta-owned Fb to distribute malware.
“Risk actors have lengthy used fraudulent advertisements as a vector to focus on sufferers with scams, malvertising, and extra,” WithSecure researcher Mohammad Kazem Hassan Nejad mentioned. “And with companies now leveraging the achieve of social media for marketing, attackers have a brand new, highly-lucrative form of assault so as to add to their arsenal – hijacking industry accounts.”
Cyber assaults concentrated on Meta Industry and Fb accounts have won reputation during the last yr, courtesy of task clusters corresponding to Ducktail and NodeStealer which might be recognized to raid companies and people running on Fb.
A number of the strategies hired through cybercriminals to realize unauthorized get entry to to person accounts, social engineering performs a vital position.
Sufferers are approached thru more than a few platforms starting from Fb and LinkedIn to WhatsApp and freelance activity portals like Upwork. Some other recognized distribution mechanism is using seek engine poisoning to spice up bogus device corresponding to CapCut, Notepad++, OpenAI ChatGPT, Google Bard, and Meta Threads.
A component that is commonplace to those teams is the abuse of URL shortener products and services, Telegram for command-and-control (C2), and legit cloud products and services like Trello, Discord, Dropbox, iCloud, OneDrive, and Mediafire to host the malicious payloads.

The actors at the back of Ducktail, as an example, leverage lures associated with emblem and advertising initiatives to infiltrate people and companies that perform on Meta’s Industry platform, with new assault waves using activity and recruitment-related issues to turn on the an infection.
In those assaults, doable objectives are directed to bogus postings on Upwork and Freelancer thru Fb advertisements or LinkedIn InMail, which, in flip, include a hyperlink to a booby-trapped activity description record hosted on probably the most aforementioned cloud garage suppliers, in the long run resulting in the deployment of the Ducktail stealer malware.
“Ducktail malware steals stored consultation cookies from browsers, with code particularly adapted to take over Fb industry accounts,” Zscaler ThreatLabz researchers Sudeep Singh and Naveen Selvan famous in a parallel research, pointing out the accounts promote for any place between $15 to $340.
“The ‘merchandise’ of the operation (i.e. hacked social media accounts) feed an underground economic system of stolen social media accounts, the place a large number of distributors be offering accounts priced in step with their perceived usefulness for malicious task.”
Make a selection an infection sequences noticed between February and March 2023 have concerned using shortcut and PowerShell recordsdata to obtain and release the general malware, illustrating the attackers’ persisted evolution in their techniques.
The experimentation additionally extends to the stealer, which has been up to date to reap a person’s private knowledge from X (previously Twitter), TikTok Industry, and Google Advertisements, in addition to leverage the stolen Fb consultation cookies to create fraudulent advertisements in an automatic style and procure increased privileges to accomplish different movements.
A number one approach used to takeover a sufferer’s compromised account is through including their very own e mail cope with to that account, therefore converting the password and e mail cope with of the sufferer’s Fb account to fasten them out of the provider.
“Some other new function noticed in Ducktail samples since (no less than) July 2023 is the use of RestartManager (RM) to kill processes that lock browser databases,” WithSecure mentioned. “This capacity is regularly present in ransomware as recordsdata which might be in-use through processes or products and services can’t be encrypted.”
What is extra, the general payload is obscured the use of a loader to decrypt and execute it dynamically at runtime in what is observed as an try to incorporate tactics aimed toward expanding research complexity and detection evasion.
Probably the most different strategies followed through the danger actor to impede research surround using uniquely generated meeting names and the reliance on SmartAssembly, bloating, and compression to obfuscate the malware.
Zscaler mentioned it noticed circumstances the place the crowd initiated touch by means of compromised LinkedIn accounts that belonged to customers running within the virtual advertising area, a few of whom had greater than 500 connections and 1,000 fans.
Hit upon, Reply, Give protection to: ITDR and SSPM for Entire SaaS Safety
Uncover how Identification Risk Detection & Reaction (ITDR) identifies and mitigates threats with the assistance of SSPM. Discover ways to protected your company SaaS programs and give protection to your information, even after a breach.
“The prime quantity of connections/fans helped lend authenticity to the compromised accounts and facilitated the social engineering procedure for danger actors,” the researchers mentioned.
This additionally highlights the worm-like propagation of Ducktail during which LinkedIn credentials and cookies stolen from a person who fell sufferer to the malware assault is used to login to their accounts and speak to different objectives and expand their achieve.
Ducktail is alleged to be probably the most many Vietnamese danger actors who’re leveraging shared tooling and techniques to tug off such fraudulent schemes. This additionally features a Ducktail copycat dubbed Duckport, which has been lively since past due March 2023 and plays knowledge stealing along Meta Industry account hijacking.
It is price declaring that the marketing campaign that Zscaler is monitoring as Ducktail is if truth be told Duckport, which, in step with WithSecure, is a separate danger owing to the diversities within the Telegram channels used for C2, the supply code implementation, and the truth that each the lines have by no means been dispensed in combination.
“Whilst Ducktail has dabbled with using faux branded web sites as a part of their social engineering efforts, it’s been a commonplace methodology for Duckport,” WithSecure mentioned.
“As a substitute of offering direct obtain hyperlinks to record internet hosting products and services corresponding to Dropbox (which would possibly carry suspicion), Duckport sends sufferers hyperlinks to branded websites which might be associated with the emblem/corporate they are impersonating, which then redirects them to obtain the malicious archive from record internet hosting products and services (corresponding to Dropbox).”
Duckport, whilst according to Ducktail, additionally comes with novel options that amplify at the knowledge stealing and account hijacking features, and in addition take screenshots or abuse on-line note-taking products and services as a part of its C2 chain, necessarily changing Telegram as a channel to go instructions to the sufferer’s device.
“The Vietnamese-centric component of those threats and prime level of overlaps in relation to features, infrastructure, and victimology suggests lively running relationships between more than a few danger actors, shared tooling and TTPs throughout those danger teams, or a fractured and service-oriented Vietnamese cybercriminal ecosystem (similar to ransomware-as-a-service style) focused round social media platforms corresponding to Fb,” WithSecure mentioned.




 #shorts #shortsfeed #nature #youtubeshorts #iciness
#shorts #shortsfeed #nature #youtubeshorts #iciness